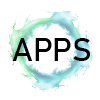The EncryptedB database stores long lists of TimeStamps and GPS Coordinates and it’s tempting to think that they must be accurate.
A closer look a the data reveals that there are sometimes hundreds of records with the same timestamp. Usually, all of the records with the same timestamp are from roughly the same location. They are though, too far apart to be seen by a device with a relatively low power antenna.
It makes sense then, that these records are downloaded to the device from Apple (Harvested) as a way to augment the devices knowledge about the area, in the same way that it may download local restaurants or weather and traffic information.
The trouble with trying to use these records as evidence is that both the timestamps and location are pretty vague. If your entire goal though is to prove a device was near a particular area at roughly a certain time then surely these records are good then right?
I’m afraid not.
I decided to test how good this data is by comparing it to the Cache.sqlite data which I know to be a pretty accurate record of a devices location.
So I mapped out all locations from cache (in gold) and also mapped out the locations from EncryptedB (WiFi in red / Cell Tower in orange).
I then searched the Cache records for a timestamp that was within a few seconds of the timestamps in EncryptedB.
For example; if I had 800 records from EncryptedB at 13:14:18 on 1st Jan 2021 I would look for a Cache record for roughly the same time, give or take a few seconds.
If I found a record that was close enough to a match, I drew a line on the map between the EncryptedB record and the Cache record.
As expected, many of the EncryptedB records were downloaded to the device when the device was in the vicinity.
But then I found something a little unusual.
My test device doesn’t have a SIM card, so usually it has no data connection. (This is important to know). I left my home and went first for coffee and then to run some errands.
What I found, is that when I connected to a WiFi source at coffee, my device took the opportunity to download a bunch of records for the location I had come from.
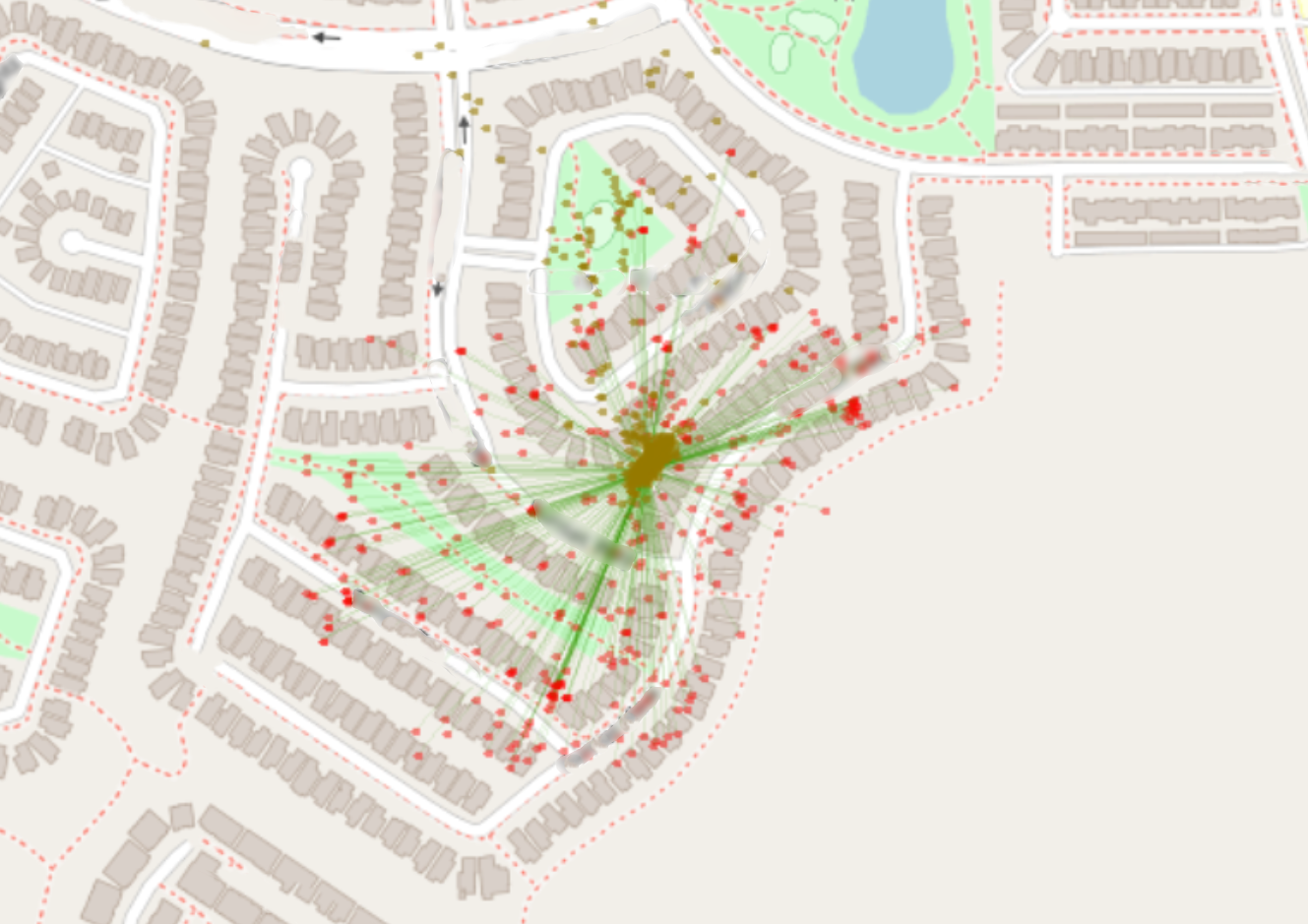
You can see on this image how GPS records at #1 were actually downloaded while I was
at #2. And that the records from #3 were downloaded when I was back at #1.
This means that the timestamp shown on these EncyptedB records is the time I connected to the Internet and is NOT the time I was in that physical location.
I will also point out that the map above shows lots of records from the Cell Tower table. But these are not the actual location of the Cell Towers.
OK, so maybe this was just because I didn’t have a constant data connection? Surely a device that is permanently connected to the internet is downloading on demand?
I opened up another phone to take a look and was even more surprised by the results.
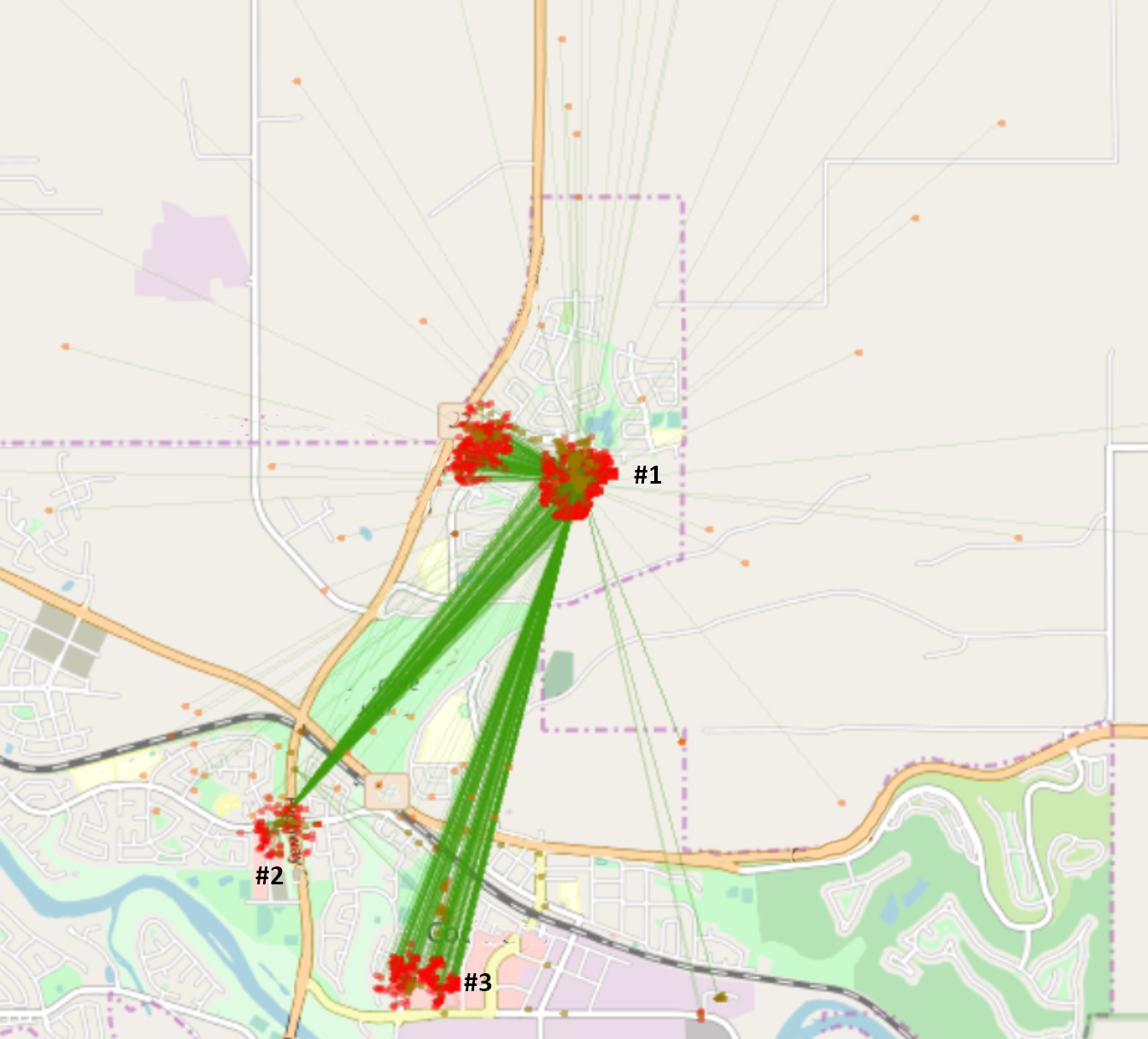
This device did have a data connection. And yet we can see that some of the EncryptedB locations are miles away from the devices actual location.
I also created the ability to filter the clusters to particular times. So I could see all records downloaded at a particular time and see the actual location of the device at that time. This showed that there were numerous times when multiple clusters, were downloaded together and that these clusters could be considerable distances apart.
I don’t know if this behaviour is filling in some blanks that exist in the database or is the result of predictions being made and frankly I don’t care.
What I do care about is that this demonstrates that EncryptedB is an even worse indicator of device location that I had thought.
I found that ThreeBars worked in much the same way, the only difference is that instead of being private networks, ThreeBars is a list of public networks such as Schools, Libraries and Stores.
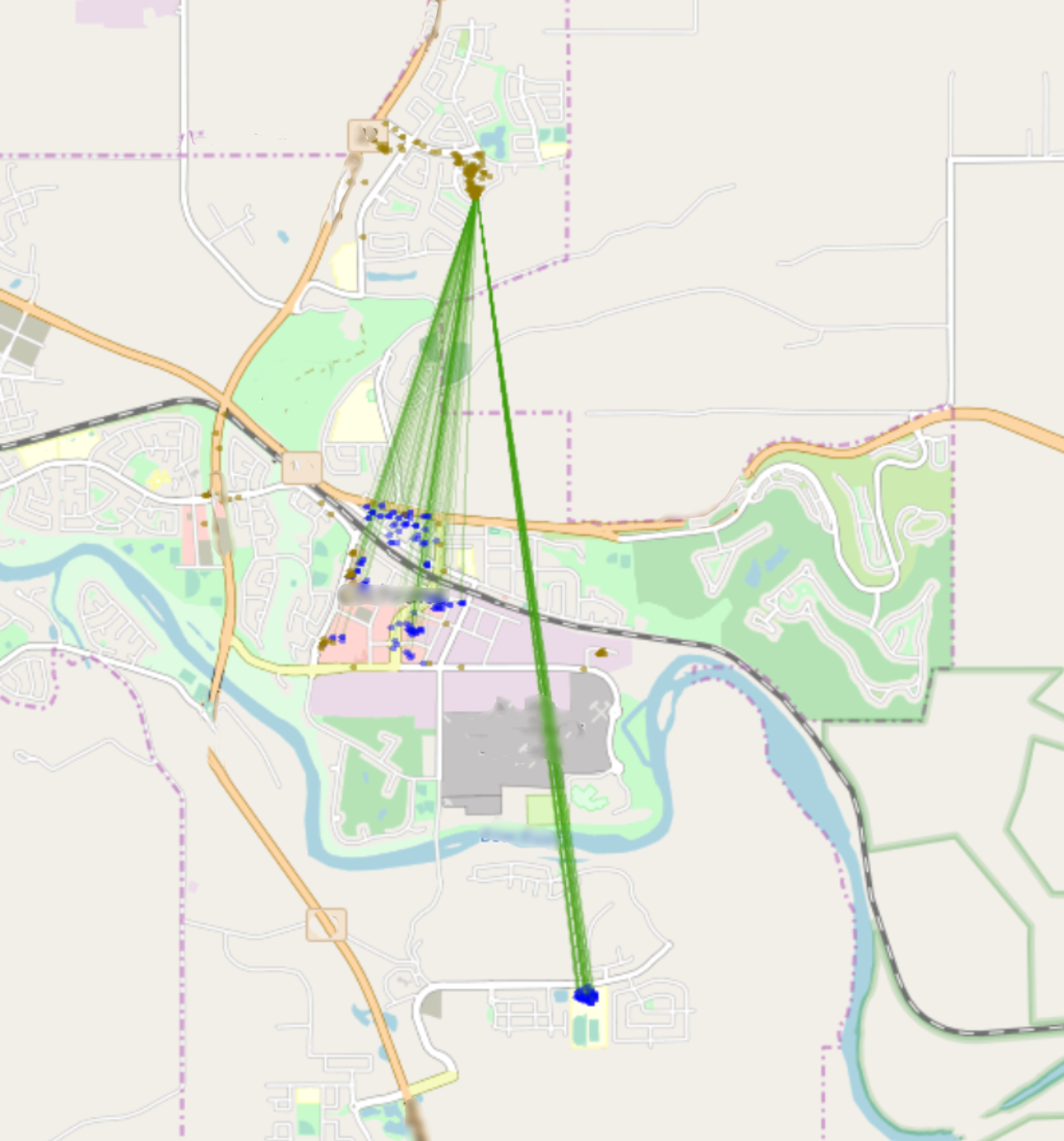
This new way of visualizing the location data really opened my eyes to exactly how inaccurate data from EncryptedB could be. If I were to find encryptedB location data in a case which was relevant to a crime scene, while I wouldn’t describe it as useless, I would be very wary of saying it’s the smoking gun.
At the very least, it demonstrates the dangers of making any kind of assumptions about why an artefact exists and the importance of trying to figure out its origins.
You can test this out for yourself in ArtEx 1.6 available now from the Software section of my site. |